The Microsoft March 2025 Patch Tuesday tackled 57 CVEs, addressing critical security flaws and emerging cyber threats. These updates are essential components of Microsoft’s security framework, playing a crucial role in safeguarding enterprise systems, cloud services, and endpoint devices against zero-day vulnerabilities and cyberattacks.
The Scope of March 2025 Patch Tuesday
The March 2025 Microsoft Security Updates assessed 57 vulnerabilities, covering categories like Remote Code Execution (RCE), Elevation of Privilege (EoP), and Security Feature Bypass, all crucial for maintaining system integrity and protecting against cyber threats.
Here’s a breakdown of key vulnerability categories addressed this month:
🔹 Remote Code Execution (RCE): 12 vulnerabilities patched, addressing unauthorized code execution risks that could allow attackers to control systems remotely.
🔹 Elevation of Privilege (EoP): 10 vulnerabilities fixed, critical because they enable attackers to gain higher access privileges, compromising sensitive data.
🔹 Security Feature Bypass: 8 instances resolved, where attackers could bypass security mechanisms, making systems vulnerable to exploitation.
🔹 Information Disclosure: 7 vulnerabilities corrected, potentially exposing sensitive data that could be leveraged in further cyberattacks.
🔹 Other Vulnerabilities: 20 issues addressed, involving Denial of Service (DoS), spoofing attacks, and other security concerns affecting business continuity.
Key CVEs Addressed in Microsoft March 2025 Patch Tuesday Updates
The Microsoft March 2025 Patch Tuesday introduced security updates for several critical vulnerabilities affecting Windows systems, enterprise applications, and cloud services. Below are the most critical CVEs, all marked as “Exploitation More Likely”, making them high-priority for patching.
CVE-2025-24035 – Windows Remote Desktop Services Vulnerability
- Impact: Allows remote execution of malicious code.
- Severity: Critical (8.1 CVSS Score)
- Description: Attackers can exploit RDS to gain unauthorized control of remote systems without user interaction.
CVE-2025-24044 – Windows Win32 Kernel Subsystem Vulnerability
- Impact: Enables privilege escalation and full system compromise.
- Severity: High (7.8 CVSS Score)
- Description: A flaw in the Win32 Kernel Subsystem allows attackers to execute code at a higher privilege level, potentially taking over the entire system.
CVE-2025-24045 – Windows Remote Desktop Services Vulnerability
- Impact: Remote code execution (RCE) attack on RDS environments.
- Severity: Critical (8.1 CVSS Score)
- Description: Exploitation of this vulnerability can lead to unauthorized system access and network-wide compromise.
CVE-2025-24061 – Windows Mark of the Web (MOTW) Vulnerability
- Impact: Bypasses security warnings for downloaded files.
- Severity: High (7.8 CVSS Score)
- Description: Attackers can exploit this flaw to deliver malicious payloads without triggering security alerts, increasing the risk of cyberattacks.
CVE-2025-24066 – Windows Kernel-Mode Drivers Vulnerability
- Impact: Allows elevation of privilege and potential system takeover.
- Severity: High (7.8 CVSS Score)
- Description: An attacker with limited user access can exploit this vulnerability to gain administrative control over a system.
CVE-2025-24067 – Microsoft Streaming Service Vulnerability
- Impact: Can be exploited for code execution within the streaming service.
- Severity: High (7.8 CVSS Score)
- Description: A flaw in Microsoft’s streaming service could allow attackers to execute unauthorized code, potentially affecting enterprise media and communication services.
CVE-2025-24995 – Kernel Streaming WOW Thunk Service Driver Vulnerability
- Impact: Privilege escalation vulnerability affecting kernel streaming.
- Severity: High (7.8 CVSS Score)
- Description: Exploiting this vulnerability can allow attackers to manipulate kernel operations, potentially leading to complete system control.
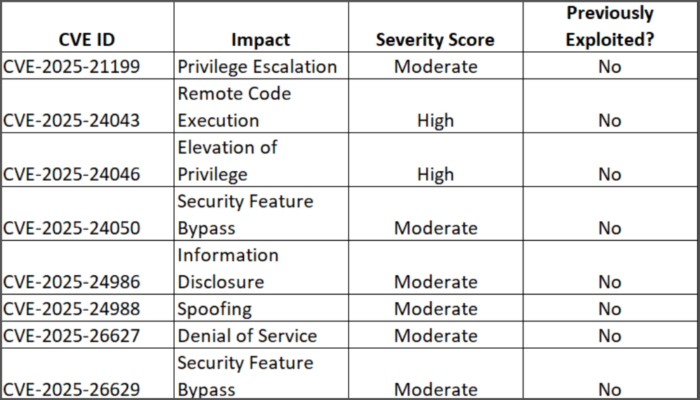
Implementing Microsoft March 2025 Patch Tuesday Security Updates
For the effective application of the Microsoft March 2025 Patch Tuesday security updates, follow these streamlined steps to ensure maximum protection against cyber threats and zero-day vulnerabilities.
1. Prioritization and Testing
🔹 First, identify and prioritize patches for critical vulnerabilities, especially remote code execution (RCE) and elevation of privilege (EoP) vulnerabilities.
🔹 Test these updates in a controlled environment to avoid system disruptions and compatibility issues before full deployment.
2. Automated Deployment
🔹 Automate patch deployment across your IT infrastructure to ensure updates are applied on schedule and without manual intervention delays.
🔹 This reduces the risk of human error and allows IT teams to focus on other security priorities instead of manual patching workflows.
3. Monitoring and Documentation
🔹 After deployment, continuously monitor systems for anomalies or patch failures that could leave exploitable gaps.
🔹 Keep detailed records of all patches for compliance audits and security reporting, ensuring regulatory adherence.
Conclusion
The Microsoft March 2025 Patch Tuesday update addressed 57 vulnerabilities, including remote code execution (RCE), elevation of privilege (EoP), and security feature bypass vulnerabilities.
These vulnerabilities impacted key services like Windows Remote Desktop Services, Kernel-Mode Drivers, Microsoft Streaming Services, and Microsoft Management Console, underscoring the ongoing need for proactive patch management and continuous security monitoring.
By minimizing manual intervention and patching delays, organizations can reduce their exposure to cyber threats while improving operational efficiency.
For more information, Contact us to schedule a personalized demo or explore additional security resources.


