Patching is an endless and often thankless job, and usually, just as you’re finishing up, there’s no time to sit back and rest on your laurels—because it’s time to start all over again.
Automation is the key to breaking free from the cycle (somewhat) while still getting everything patched quickly. And to some extent, most OS vendors today offer solutions that promise to make patching simpler via automation. But how well do they actually work?
Given that Windows is today’s leading desktop OS, under the hood of almost 80% of the world’s desktop PCs, many organizations use one of the three available tools provided by Microsoft: SCCM, WSUS, or the newest contender, Intune.
Before we even begin exploring Windows patching, it’s worth stopping to ask the broader question of why a single vendor, Microsoft, has seen fit to produce three different tools, each with its own focus area, in its attempt to solve the same problem—patching.
With that in mind, let’s take a dive into all three of these options, including how well they perform when it comes to taking the “heavy lifting” of patching off your team’s shoulders.
Three Microsoft Solutions
Supporting Windows endpoints can be confusing because Microsoft alone offers three different choices. How do you know which one is right for you? And, of course, the more critical question: Do any of the choices offer a one-stop solution that will take care of your entire environment?
The answer to this will depend in part on whether you’re looking for a single-purpose or multi-purpose tool, how much you want to get into the nitty-gritty of your systems (scripting vs. UI-based), and the types of endpoints you’re supporting (local, cloud, mobile).
Let’s look at all three solutions, including what they do best and their limitations.
Microsoft System Center Configuration Manager (SCCM)
- What Microsoft says it is: “An integrated solution for managing all of your devices.”
SCCM is actually not a patching tool at all but a very powerful configuration manager. With the latest versions, SCCM has been wrapped up in Microsoft’s Endpoint Manager (MEM) suite of tools, which, confusingly, includes Intune (which we’ll look at a bit later).
Embedded within SCCM are features that allow system administrators to set up software updates, or patches. Microsoft refers to this subset of SCCM’s features as “a set of tools and resources that can help manage the complex task of tracking and applying software updates to client computers in the enterprise.”
- What it does best: Powerful management of and deployment to a wide range of Microsoft endpoints, from on-premises servers and workstations to cloud-based Azure configurations; simple automation.
- Where it falls short: A full management suite, making it expensive and complex since it offers far more than just patching; limited reporting and lack of real-time monitoring sometimes necessitate third-party add-on solutions.
- Patching: This complex product does offer some patching features, but drilling down and deploying them can be confusing and time-consuming; does not natively support patching for non-Microsoft products; best for larger jobs in on-premises networks due to its power and automation features.
Windows Server Update Service (WSUS)
- What Microsoft says it is: “[F]ully manage the distribution of updates that are released through Microsoft Update to computers on your network.”
Unlike SCCM, WSUS is designed only for software updates and is therefore a dedicated patching tool. Plus, it’s free, making it an attractive choice. It can download updates once and then roll them out to large numbers of systems across your entire environment, saving bandwidth and automating the update implementation.
You can also use WSUS to run limited testing on new updates before rolling them out across your organization. However, because WSUS is hard to configure and implement on its own (even with the Microsoft-provided configuration wizard), it’s primarily seen as a component that can be integrated into other security solutions. (For instance, WSUS is an integral part of SCCM and many other security solutions, where it is often hidden from the user.)
- What it does best: Free service (included with Windows license); supports a range of Windows systems and multiple patch types including other Microsoft apps; easily scalable to handle very large Windows environments.
- Where it falls short: A bare-bones app aimed primarily at on-premises environments; difficult to impossible to roll out across cloud-based or more diverse configurations; no GUI provided, limited reporting, difficult setup, plus inventory management is very limited with poor scanning accuracy.
- Patching: WSUS supports third-party patches if you subscribe to their update catalogs, but this can be complicated to configure and isn’t always executed gracefully in practice; also, limited scheduling and reporting capabilities, meaning you’ll be doing most of the work manually; best for smaller, local networks.
Intune
- What Microsoft says it is: “[A] cloud-based service that focuses on mobile device management (MDM) and mobile application management (MAM).”
Intune, like SCCM, is a full-featured configuration management and policy tool that attempts to secure your entire organization by creating access policies for cloud and BYOD devices. That means it has a lot more features than WSUS, not just patching. In fact, patching isn’t a native capability of Intune at all. Instead, patches are rolled out through Windows Update for Business (WufB – for Windows systems only), and then update settings are configured through Intune (full instructions from Microsoft here).
-
- What it does best: BYOD, mobile, cloud, predefined policies; integrates with other solutions, primarily for mobile and cloud; works best with Windows systems, some other capabilities.
- Where it falls short; Paid subscription model; limited support for third-party software, no OS updates for non-Windows OSes; inflexible dashboard, difficulty deploying drivers.
- Patching: Unlike WSUS and SCCM, Intune does not support patching for a slightly wider range of OSes and third-party software; is the only product of the three mentioned here that natively supports patching in the cloud; best for cloud-based management of Microsoft OSes and products.
In case you’re confused by the relationship between Intune and SCCM, Microsoft has provided this diagram showing how both are integrated into its Microsoft Endpoint Manager ecosystem:
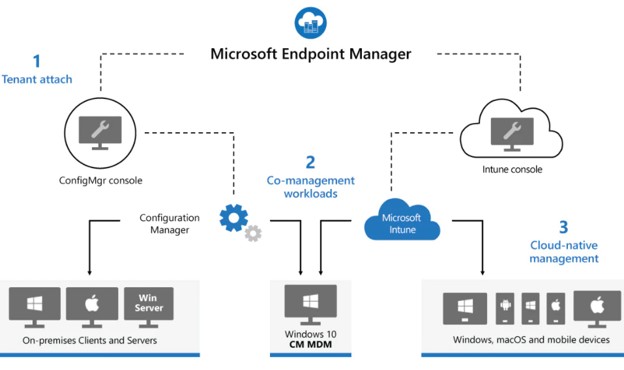
Figure 1: Microsoft’s SCCM and Intune as part of the Endpoint Manager ecosystem (Source: Microsoft).
As can be clearly seen in Figure 1, Microsoft’s big-picture vision is for its enterprise clients to use SCCM for on-premises clients and servers while it also supports Windows, macOS, and mobile devices with Intune.
The Elephant in the Room
While all of these solutions have their own strengths and weaknesses, Microsoft has been almost completely silent on the biggest question of all: How do these three options handle non-Windows operating systems and software?
In the case of WSUS and SCCM, the answer is simple: They don’t. For Intune, things are a bit more complex. As Microsoft’s BYOD and cloud solution, Intune is the most flexible of these three options and supports some monitoring and supervision of macOS, iOS, and Android systems.
However, when it comes to Linux distributions, Intune offers no capability other than a workaround (MEM expert Peter van der Woude offers five possible workarounds in this post if you must use Linux with Intune-secured business environments).
In October 2020, on the community discussion boards for Microsoft Endpoint Manager, a user asked about managing Linux computers with MEM/SCCM, and a Microsoft employee replied, “Full management within Microsoft Endpoint Manager of Linux is under investigation and is a strong desire of Microsoft’s but we’ve made no commitments and have no timeline for this.” This doesn’t sound like the kind of strong, unequivocal support you need as a system administrator when choosing a patching solution to secure 100% of your endpoints. Especially considering that well over 40% of all sites worldwide are hosted on Linux systems (and only around 25% on Windows).
Another popular alternative is a configuration management tool that can handle a variety of endpoints. However, just as with Microsoft’s own SCCM, those come with a big price tag and are complicated to implement. CM tools are overkill if you’re just looking for a way to simplify and automate patching.
When planning from the ground up, it makes sense to choose a solution that can make patching as simple as possible, with automation and intelligent deployment across all your endpoints, including Windows, Linux, and legacy Unix systems, both on-premises and in the cloud.
How to Simplify Windows Patching (and Beyond)
When it comes to Windows systems, JetPatch actually makes use of WSUS’s powerful features, but it goes much further than any of Microsoft’s three solutions can by integrating your Windows systems with all your other devices, environments, and endpoints in a single dashboard view. All WSUS interaction is controlled by JetPatch via its intuitive interface – no need to access WSUS.
Patching is never going away, and it can be a thankless task. So why harness yourself to tools that only handle part of the job? With JetPatch in your corner, you’ll be able to take care of patching faster and with fewer hassles. Find out how JetPatch can take away the pain of patching—for Windows systems and beyond.



