What does an ideal patch management system look like? We have had many discussions with JetPatch customers about what capabilities they would like to see in a patch management platform. Over time, we compiled a list — we call it the ultimate patch management checklist. We thought it would be useful to share what we heard from IT security teams and CISOs. So, without further ado, the ultimate patch management checklist.
Centralized Patch Management Through a UI
The modern enterprise has thousands of servers, numerous server groups, OSs and endpoints of many kinds, such as desktops, laptops, and mobile devices. Thus, a modern patch management platform should handle all patch management tasks across all environments with a single, visual user interface.
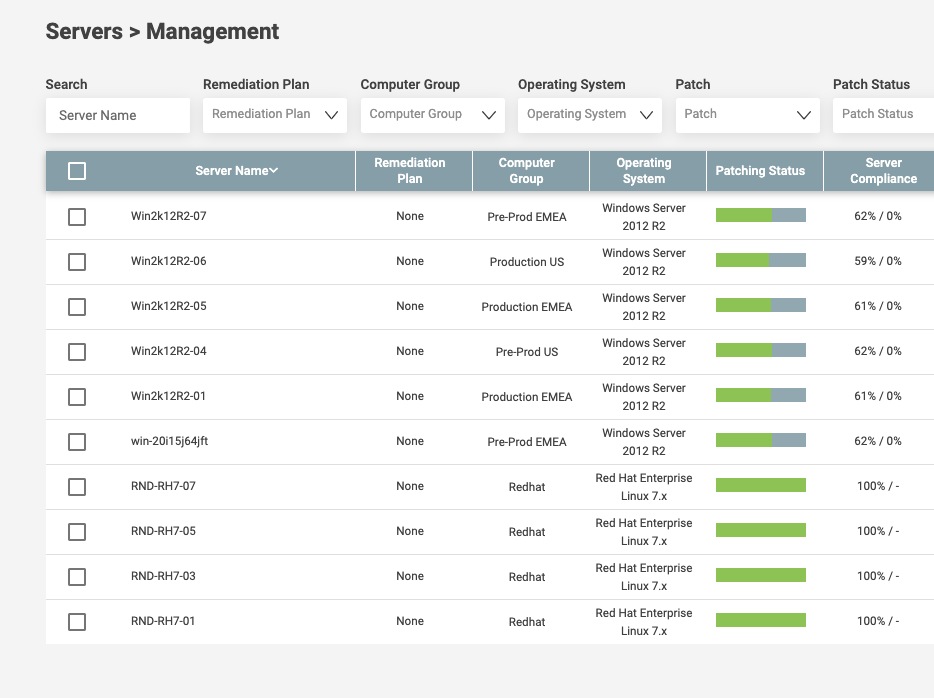
Real-Time Patch Compliance Reporting
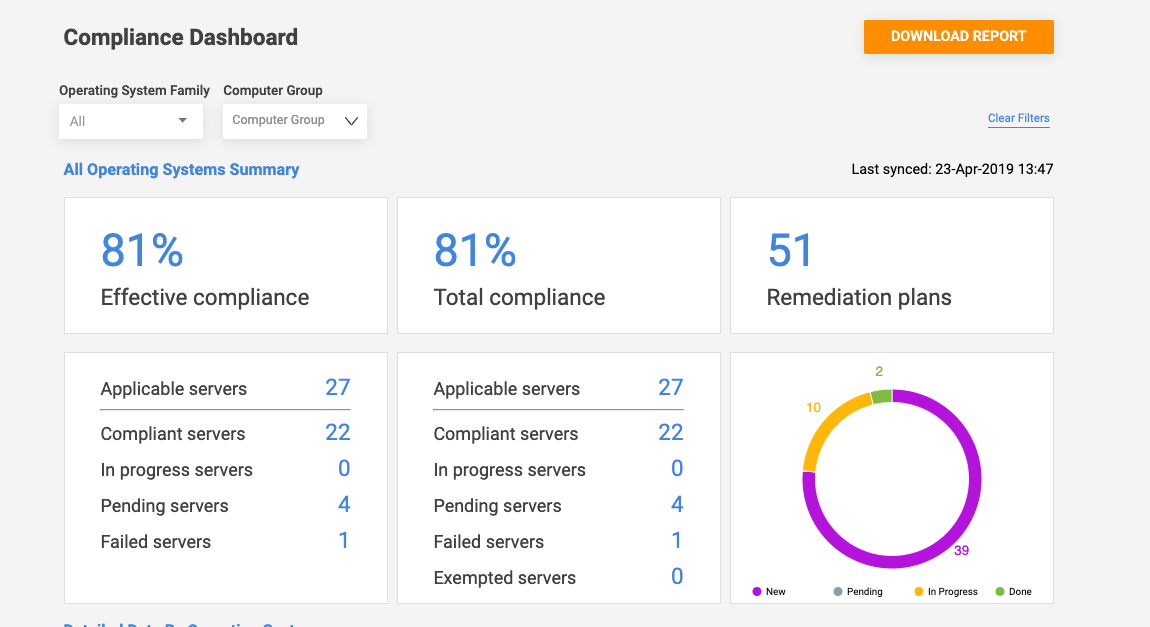
IT, DevOps and the CISO need to know where they stand right now with potential vulnerabilities. A good patch management software should have an up-to-the-minute dashboard that shows patching compliance across all the organization’s endpoints, and their compliance with regulatory requirements or the organizations’ own policies.
Standardized Patching Process Across Environments: Cloud, On-Premise and Heterogeneous OSs
A patch management platform should have the ability to define and execute a unified patching process regardless of the environment in which the patches are being deployed. This includes different OSs, such as macOS, iOS, Windows or Android, as well as multiple public clouds and hybrid environments.
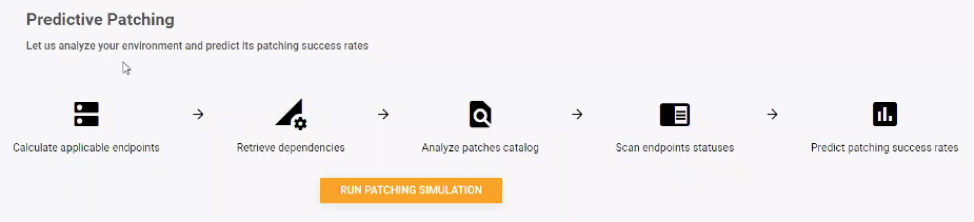
Predictive Patching
Patches fail for many reasons, such as machines that are turned off, invalid credentials, expired licenses, and unknown dependencies. The vast majority of these preventive issues are only discovered after attempting to implement the patching cycle. As patching cycles might take hours to run and are performed in a strict downtime window, failing to achieve a 100% first-pass patch success rate results in one of two outcomes:
- Patches are not remediated until the next maintenance window (by which time more things may have changed or broken), leaving the endpoints vulnerable
- Another downtime window needs to be scheduled, potentially hurting the business
The most advanced patch management platforms have a “predictive patching” capability that allows IT teams to run a simulation of the patching process before deploying the actual patch cycle. Such a simulation quickly exposes any potential problems that might occur during the patching cycle.
Patch Consolidation
Instead of deploying patches individually, the ideal patch management platform should be able to intelligently consolidate the deployment of multiple patches at the optimal time. This can be done by both organizational policies, as well as techniques such as machine learning. The result is shorter downtimes while minimizing the length of time vulnerabilities remain unpatched.
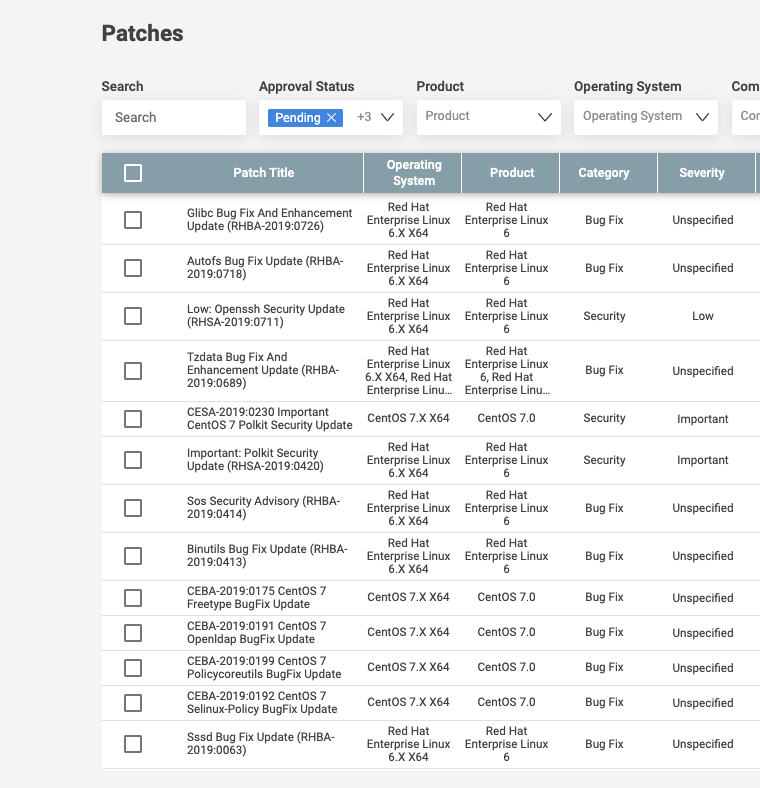
Patch Recommendations based on Industry Benchmarking and Baseline Comparisons
Patch management systems must leverage respected industry vulnerability databases, such as CVE, NIST NVD, as well as vendor-provided databases, to ensure continuous baseline and patch available tracking. They should also provide recommendations based on patch severity and possible business impact for proper patch management prioritization.
Customizable Scripts for Pre- and Post-Patching Processes
Proper patch management and vulnerability remediation are about a lot more than simply deploying patches. They involve many more steps that need to take place before patching, such as backups, and after patching, such as rebooting, testing and rollbacks (if necessary). The ideal patch management software should be able to collect and manage runnable scripts targeted for endpoints by creating tasks and workflows for pre-patching and post-patching activities.
Automated Multi-Patch Deployment
Because of the need for so many patches, deploying each one individually would be time-consuming and inefficient. An enterprise-grade patch management system should intelligently aggregate patches based on endpoint and severity, and roll out more efficient multi-patch workflows by server groups and maintenance windows.
Integration of Patch Processes with the Organization’s ITSM System
Next on our patch management checklist is an importan,t but often overlooked capability: integration with ITSM. Patch management is not an island in the enterprise IT world. An enterprise-grade patch management platform should be able to automatically create tickets — for example, for patch deployment approvals or patch-related incidents — in the organization’s ITSM, such as ServiceNow, JIRA, and CA Service Desk Manager.
Integration with Vulnerability Scanners
Integration with external vulnerability scanning and assessment tools such as Rapid7 Nexpose, Tenable Nessus, or Qualys, provides an in-depth assessment and report of discovered vulnerabilities, which a patch management platform should be able to act on automatically or semi-automatically (i.e., awaiting human approval). Learn more about this in our post on best practices in patch management.
Role-Based Access Control (RBAC) and Integration with Domain Controller
Patch management systems should provide the ability to control who accesses what, ideally, working with the organization’s already defined roles and permissions via integration with a domain controller such as Active Directory or LDAP. Types of access should include local user, domain user, and domain-group. In addition, access defined by endpoint scope must be available.
Patch Optimization and Exception Handling
A good patch management system should be able to analyze and learn the root causes of remediation delays and failures, such as poor visibility into software assets, and automatically correct them.
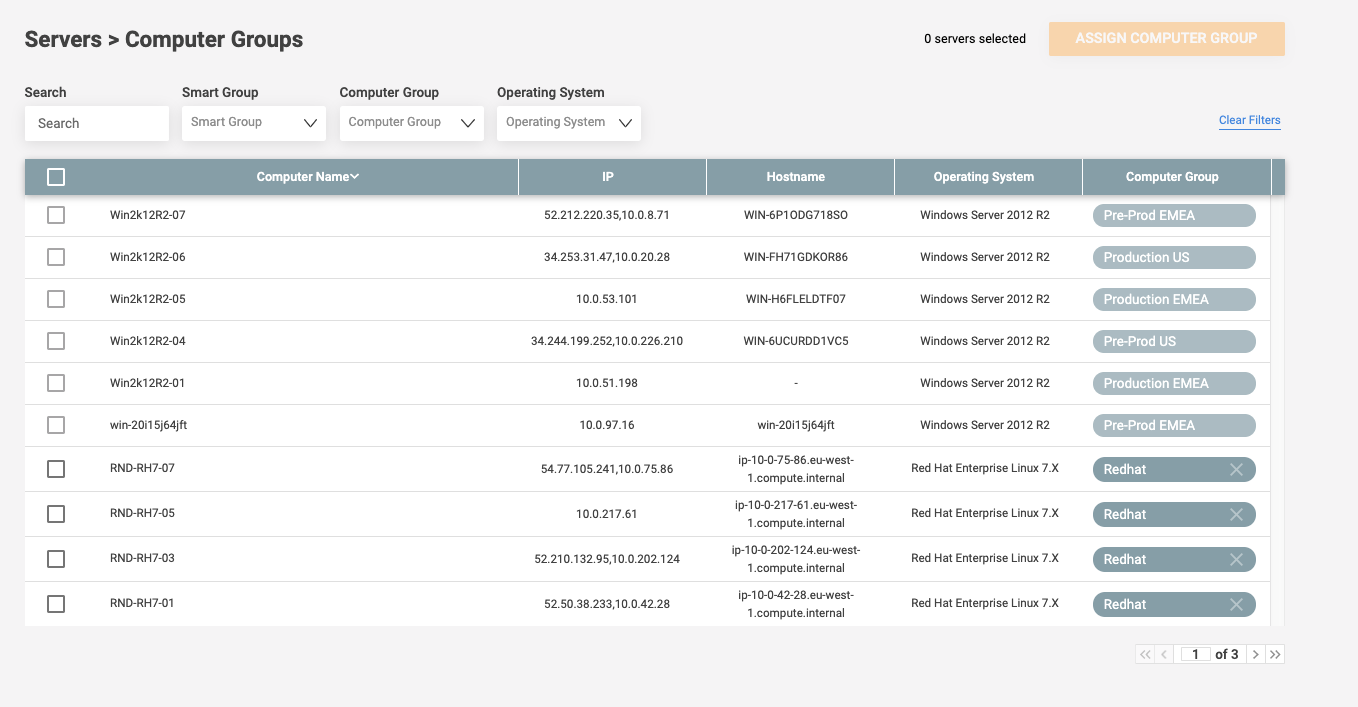
Filtered Views Based on Endpoint Groups
IT and DevSecOps teams need to have an easy way to monitor and act on different groups of endpoints. A must-have, therefore, for a modern patch management system, is the ability to aggregate devices by endpoint groups — such as by OS, hostname, IP address or tags. Ideally, it will be able to save multi-filter groups.
Related Reading
To learn more about this topic read our post The Three Principles of Patching: Ignore at Your Own Peril.
Patch Management Checklist: What Next?
We hope you found this patch management checklist useful as you look for the best patch management platform for your organization. JetPatch, of course, supports all of these features and more. We would love to show you: Request a demo.



