If you think patching is important, you’re not alone. In fact, there’s widespread agreement across most industries, with many OS vendors and software companies now clued in to the importance of patching. It’s easy to see that these companies are working hard to give you frequent, regular patch releases. So it’s no surprise that patching has become a big part of the security conversation.
What is a surprise, however, is that it doesn’t seem to have halted the number of breaches taking place, even though patches are available, with large companies still being hacked. Air India, for example, had data for 4.5 million customers leaked in May 2021, and McDonald’s exposed confidential employee and customer information in a June 2021 breach. Even the most tech-savvy companies are vulnerable, like gaming company Electronic Arts, which had sensitive source code stolen in a June 2021 hack.
Given that up to 60% of breaches are due to known vulnerabilities, how could breaches like these still be happening when patches have been available, in some cases for a very long time.
There are a few major reasons:
- Most organizations aren’t automatically detecting new hardware/software when it comes into the network, leaving it to network admins to manually update.
- A large number of organizations perform vulnerability scanning only once a month or less.
- Over one-quarter of organizations don’t get around to patching within a month of a patch’s release date.
Sometimes, patches might exist but not be rolled out for a variety of reasons: the complexity of the enterprise ecosystem, the siloing of IT and security, or application owners refusing updates due to the risk of interfering with business continuity. Of course, none of this even touches on the massive number of new vulnerabilities being discovered all the time, making it a serious challenge to keep up—or even put in the time it takes to analyze resources and prioritize available patches.
But there’s a single dirty secret behind all these explanations: Patching is seen as a “necessary evil”—not a part of the organization’s overall business plan. And the reason it’s not viewed as mission-critical? Because most organizations have a low level of maturity when it comes to IT.
Luckily, maturity is quickly becoming an in-demand metric in a range of areas since it can help provide a bigger-picture view, helping to hone aspirations and strategy for future development. And advancing the organization to a higher level of maturity for IT can have a number of other benefits beyond patching.
Let’s take a look at the concept of IT maturity and see where patching fits into the big picture—and how you can help IT across your organization move toward greater maturity, meaning greater overall safety as well.
The Road to IT Maturity
While different organizations may use slightly different models, according to one popular version promoted by IBM, the maturity of an organization’s IT program can be measured across five stages:
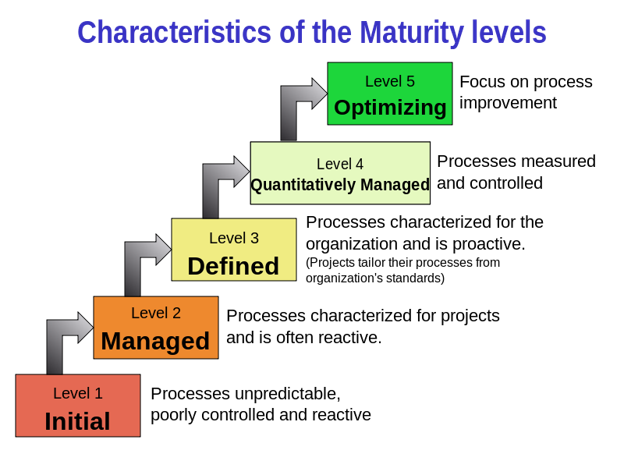
Figure 1. A commonly accepted model of maturity levels. (© Sally Godfrey via Wikimedia)
1. Initial
An IT department at this initial stage of maturity development is characterized by ad hoc management. You’ll know you’re at this level if you feel like you’re constantly putting out fires, as emergencies and unforeseen circumstances crop up more often than they should, and there’s little time to sit back and evaluate lessons learned for the next time. Within the organization as a whole, IT is viewed as a cost center and burden rather than as a driver of business value.
- IBM description: “No standards are in place and inconsistency exists across the organization.”
- SANS description: “Policy and standards are undocumented or in a state of change.“
- Patching position: This is a very siloed state and therefore the riskiest in terms of patching. If there’s little business justification for IT, then patching is seen as interfering with business activities while at the same time not driving business value. So it will be given a very low priority.
- Primary patching challenge: Raising awareness, avoiding chaos, rising above “putting out fires.”
2. Managed
An IT department at this maturity level may surprise you by running smoothly most of the time. Basic IT functions are being fulfilled, and there may even be some formalization of interactions between IT and business. Most processes have clear owners, but problems may still be handled on a putting-out-fires basis. There are still numerous “unforeseen” circumstances to deal with.
- IBM description: “A process is in place and activities are managed, but the process is orchestration without insights.”
- SANS description: “Policy and standards are defined in specific areas as a result of a negative impact on the program rather than based on a deliberate selection of best practices or standards from recognized frameworks.“
- Patching position: While at this level, organizations may pay lip service to patching and even define this as an essential role of IT, siloing is still in place, which may cause a lack of communication between departments. This means patching will often have to take a back seat due to other processes seen as more “mission critical.”
- Primary patching challenge: “Keeping the lights on,” maintaining policies, following defined procedures without a great deal of automation, getting tooling in place.
3. Defined
This level is recognizable by the extent of the interactions between IT, security, and the rest of the organization. More entity-wide controls are in place, including an enterprise-level strategy and greater collaboration. For instance, at this level of maturity, there are clear IT investment decisions, transparent decision-making, and business interactions for all critical functions.
- IBM description: “A process is defined as a standard across the organization and is tailored for individual projects.”
- SANS description: “Policy and standards have been carefully selected based on best practices and recognized security frameworks and are updated as needed to fulfill the program’s mission. Employees are made aware of standards and training on requirements is available.”
- Patching position: Patching has a far greater chance of success at this level because IT is able to communicate and coordinate with other departments to reduce downtime and improve success rate.
- Primary patching challenge: A proactive approach is now keeping the day-to-day under control, but it’s too early to sit back and relax; automation and intelligence will lead to continuous improvement.
4. Quantitatively Managed
At this level, the organization is experiencing more efficient practices and outcomes that are probably better than the industry average. There is a clear understanding of IT investment in the C-suite, and investment is quantified and strategic rather than ad hoc (as it was at lower maturity levels).
- IBM description: “The process is measured and any deviation from the standard is addressed.”
- SANS description: “Adherence to defined policies and standards is tracked and deviations are highlighted. Training of personnel on requirements is required at least annually.”
- Patching position: With this level of support, it’s very likely that IT has been provided with dedicated tools to handle vulnerability remediation.
- Primary patching challenge: Leveraging tools in place to harvest actionable business information and track KPIs, such as time to remediation and value to the organization, to continue demonstrating ROI.
5. Optimized
An organization at this level of IT maturity realizes that it’s not content to just rest on its laurels. As a role model for others in its field, there is an emphasis on continuous improvement and implementation of state-of-the-art processes, work procedures, and tools. There is a laser focus at this level on value-centric IT management, with clear KPIs and strategic investment to drive business value and ROI.
- IBM description: “The process is continuously improved.”
- SANS description: “Automated, proactive controls enforce policy and standards and provide input to regular updates and training requirements.”
- Patching position: Full vulnerability management orchestration and remediation are in place, including automation and prediction to create a smooth-running infrastructure with as little patching-related disturbance as possible. IT has strong, continuous insight into vulnerabilities across the entire environment—on-premises and in-cloud—thanks to integrated dashboards.
- Primary patching challenge: At this level, there are very few challenges beyond tracking alerts and remediating exceptions when identified. IT security is considered an integral component when it comes to innovation, and there is strong buy-in at all levels of the organization.
Why Maturity Matters
Why bother looking at how mature your IT is?
The goal of assessing the maturity level of your company is not to penalize IT for failing to meet standards or failing to improve. It’s not about finger-pointing at all, or it shouldn’t be. It’s about shifting the mindset across the entire organization to the point where IT is managed like a business, following professional business practices.
Companies with a more mature approach to IT find themselves safer overall when vulnerabilities hit the fan, both through eliminating risks and by creating comprehensive plans for when exceptions occur.
Not only that, but cybersecurity maturity is likely to become part of certain regulatory frameworks, e.g., the U.S. DoD Cybersecurity Maturity Model Certification, which will be enforced through third-party assessments.
So there’s a good chance your organization will be called on to demonstrate the maturity of its security posture at some point in the future. And according to a recent Deloitte report, companies with a higher level of IT maturity also report higher revenue growth and profit margins.
(For a more nuanced breakdown of the stages of IT maturity when it comes to vulnerability management, check out this highly detailed post from SANS.)
JetPatch: Powering You Towards Maturity
The key to helping your organization mature is realizing that technology isn’t an end in itself, but rather, should be leveraged to solve business problems. Assessing maturity can also help control your IT budget as well as expand the budget where necessary when there is a suitable business case.
Maturity is a complex equation that takes into consideration a wide range of factors: management, processes, personnel, technology, and more. And it’s certainly not all or nothing.
Regardless of your organization’s current IT maturity level, it’s always possible to map out goals and then put processes in place to create change. This lets you choose tools that not only fit your present maturity level but also accommodate future expansion.
For instance, a vulnerability remediation tool like JetPatch offers automation, predictive analytics, and advanced insights into your entire environment. Choosing a solution like JetPatch with a modern, advanced feature set gives you a solution that can boost your organization today as well as down the road, putting you in the fast lane to IT maturity.



