By now you must be in a Log4j overdose, after reading all those articles and analyses. No doubt, this is a major zero-day event that requires your immediate attention. But, just in case, let us share with you some of the Log4j highlights and also explain how we can help you. Today. Right Now, to mitigate the situation.
Immediate Threat Call for An Immediate Action
Log4j is a logging library made by the Apache Software Foundation and is used extensively in services. The security risk found with Log4j allows hackers to execute remote commands on a target system. Not only that, it seems like exploiting this vulnerability is not very difficult and as a result, there are millions of applications, and their related services, that are at risk. And, there are multiple incidents of this vulnerability exploited in the wild, which means hackers are taking advantage of this loophole. Since the discovery, the Apache org issued a security patch of release 2.15.0 that addresses that threat. Now all you need to do is identify all the impacted services and applications and patch them…not a simple task.
To complex things even further, even though Log4j is a Linux-based vulnerability, it has to potential to impact both Linux and Windows devices. As the remote code execution (RCE) drops its payload, if able to exploit the vulnerability it can run shell scripts and use lateral movement to access multiple types of devices.
What Are Some of The Common Responses
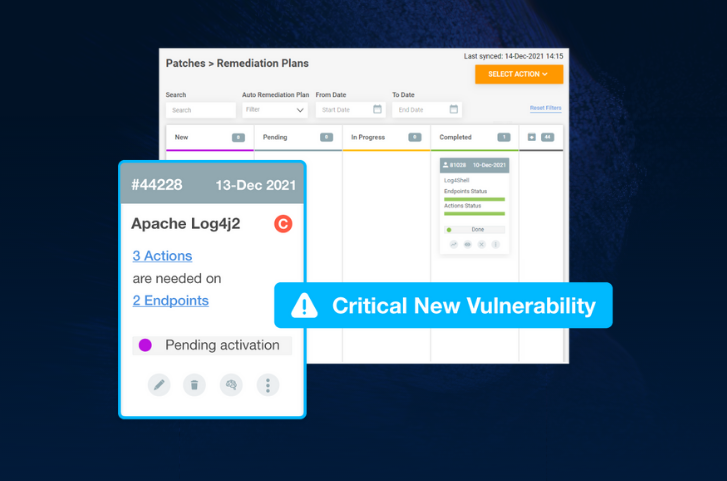
Because the list of affected applications includes some of the most popular software products out there, and it is not yet clear enough for which product a fix is needed, customers are frantically searching for a reliable source and for clear best practices to remediate the situation. For example, GitHub offers a summary of all major applications and their current status, as defined by the app vendors.
Other companies take advantage of their vulnerability scanners (e.g., Tenable) in order to highlight the questionable apps and look for a fast path to security. Although knowledge is power, in this case, the tedious effort of going application by application and device by device to mitigate the risk is overwhelming. That’s why once the allegedly compromised assets have been identified, it is time for some ‘heavy-lifting’ patching.
Automating 3rd Party Application Patching Across Your Entire Environment
Regardless of the method used to identify the potential attack vector, it is clear that patching the vulnerable applications to the latest version, sans the Log4j, is the best course of action. This is the path many companies are now exploring, especially in those cases where devices are strictly managed centrally and application updates are pushed as part of security and compliance policy.
Here is how JetPatch can help:
- We automatically deploy a light agent on all of your devices.
- We quickly identify the existing applications and their current versions.
- We source the latest versions of all applications – the non Log4j versions.
- We execute application patching automatically, following your policy, until full compliance.
CLICK HERE to find out how JetPatch can help you remediate Log4j related apps.