Microsoft July 2024 Patch Tuesday reveals Microsoft’s rigorous defense against cyber threats, introducing crucial updates to address 138 CVEs affecting a broad spectrum of its products. This effort highlights Microsoft’s proactive stance in safeguarding enterprise environments from the evolving landscape of digital threats that challenge industry norms today.
The Scope of July 2024 Updates
The July 2024 Patch Tuesday rollout corrected 138 vulnerabilities, including 5 critical remote code execution flaws out of 142 flaws and 4 zero-day vulnerabilities.
Comprehensive Vulnerability Assessment
This section provides a detailed look at the CVEs addressed in this month’s Patch Tuesday updates, categorized by their nature and potential impact:
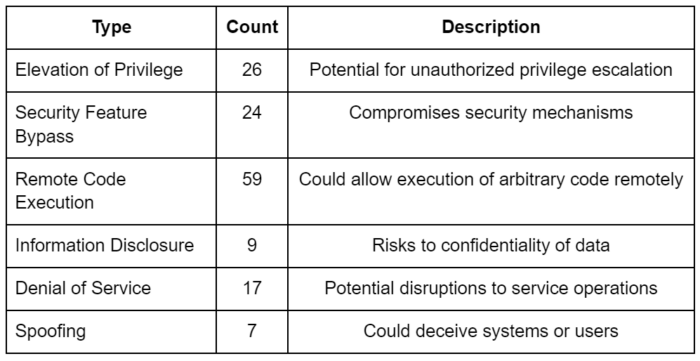
- Elevation of Privilege (EoP): 26 vulnerabilities, representing a significant portion, underscore the need for stringent access controls within systems to prevent unauthorized access escalation.
- Security Feature Bypass (SFB): 24 vulnerabilities, crucial for maintaining the integrity of security mechanisms.
- Remote Code Execution (RCE): 59 vulnerabilities, critical due to their potential to allow attackers to execute arbitrary code remotely, thus requiring immediate attention.
- Information Disclosure (ID): 9 vulnerabilities that could lead to unauthorized access to confidential information, posing significant risks to data privacy.
- Denial of Service (DoS): 17 vulnerabilities that could disrupt service operations, directly impacting business continuity.
- Spoofing (SP): 7 vulnerabilities that could deceive systems and users regarding the source of data or communication.
Key CVEs Addressed in July 2024 Updates
In-Depth Analysis of Critical and Zero-Day Vulnerabilities
- CVE-2024-38080 – Windows Hyper-V Elevation of Privilege Vulnerability
An actively exploited zero-day vulnerability in Windows Hyper-V that allows attackers to gain SYSTEM privileges. This vulnerability was given a CVSS score of 7.8 and requires immediate attention due to its active exploitation in the wild.
- CVE-2024-38112 – Windows MSHTML Platform Spoofing Vulnerability
This spoofing vulnerability in Windows MSHTML was actively exploited. It requires an attacker to send a malicious file to a victim, which the victim would need to execute. This vulnerability was publicly disclosed by Haifei Li from Check Point Research.
- CVE-2024-35264 – .NET and Visual Studio Remote Code Execution Vulnerability
A publicly disclosed RCE vulnerability affecting .NET and Visual Studio. Exploitation occurs by closing an http/3 stream while processing the request body, leading to a race condition. This vulnerability was discovered internally by Radek Zikmund of Microsoft Corporation.
- CVE-2024-37985 – Systematic Identification and Characterization of Proprietary Prefetchers (FetchBench Side-Channel Attack)
A previously disclosed side-channel attack that could steal sensitive information from heap memory. Exploitation requires specific actions to prepare the target environment.
Security Enhancements and Patch Impact
In July 2024, Microsoft demonstrated its commitment to cybersecurity with targeted updates across its product suite. Notably, Windows received the highest number of patches, reflecting its pivotal role in both enterprise and personal computing environments. This substantial focus reflects the critical need to fortify systems against advanced threats.
Secure Boot and Windows Security Enhancements
- Secure Boot Enhancements: The latest updates have improved Secure Boot’s validation processes. These enhancements are essential for verifying software integrity before the OS loads, effectively blocking rootkits and other malware at the boot level.
- Windows Security Enhancements: Significant updates to Windows Defender have enhanced its threat detection capabilities. Updated signature databases and advanced heuristic algorithms improve the system’s proactive defense mechanisms. Further, the integration with cloud-based analytics has been strengthened, enhancing real-time protection against new and evolving cyber threats.
Practical Guide: Implementing July 2024 Security Updates
Organizations must prioritize deploying patches for internet-facing systems and critical services.
Key steps include:
- Prioritization and Testing: Assess and prioritize patches based on the severity and your environment’s exposure. Conduct thorough testing in a controlled environment to prevent disruptions.
- Deployment Strategies: Utilize automated tools like JetPatch for streamlined patch deployment, ensuring that patches are applied consistently and efficiently across all systems.
- Post-Deployment Monitoring: Continuously monitor the systems for any abnormalities post-update to ensure all patches have been successfully applied and are functioning as intended.
Conclusion
This July 2024 update cycle targeted 138 key vulnerabilities, including critical remote code execution flaws and notable zero-day vulnerabilities. The CVEs affected essential services like Microsoft Windows, Office, and Azure, highlighting the necessity for comprehensive security measures.
JetPatch can enhance IT security efficiency through complete automation of the patch management lifecycle, from assessing CVEs to deploying patches. This automation not only reduces exposure to vulnerabilities but also improves operational efficiency.
Tailored to meet the specific needs of each organization, we provide meticulous control over patch scheduling and deployment tactics, ensuring that security measures are maintained and optimized.
For more information, contact us to schedule a personalized demonstration today.


