June 2024 Patch Tuesday reveals Microsoft’s rigorous defense against cyber threats, introducing crucial updates to address 51 vulnerabilities that affect a broad spectrum of its products.
This effort highlights Microsoft’s proactive stance in safeguarding enterprise environments from the evolving landscape of digital threats that challenge industry norms today.
The scope of June 2024 updates
This rollout corrected 51 vulnerabilities, including 18 critical remote code execution flaws and one zero-day vulnerability, demonstrating Microsoft’s proactive stance in combatting potential cyber threats.
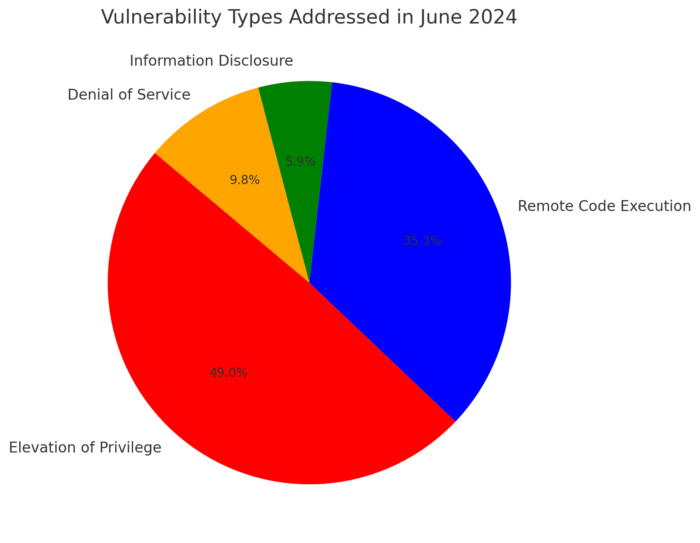
Key Vulnerabilities Addressed in June 2024 Patch Tuesday
This section provides a detailed look at the vulnerabilities addressed, categorized by their nature and potential impact:
- Elevation of Privilege: 25 vulnerabilities, representing the largest group, underscore the need for stringent access controls within systems to prevent unauthorized access escalation.
- Remote Code Execution: 18 vulnerabilities, critical due to their potential to allow attackers to execute arbitrary code remotely, thus requiring immediate attention.
- Information Disclosure: 3 vulnerabilities that could lead to unauthorized access to confidential information, posing significant risks to data privacy.
- Denial of Service: 5 vulnerabilities that could disrupt service operations, directly impacting business continuity.
Key Vulnerabilities
| Type | Count | Description |
| Elevation of Privilege | 25 | Potential for unauthorized privilege escalation |
| Remote Code Execution | 18 | Could allow execution of arbitrary code remotely |
| Information Disclosure | 3 | Risks to confidentiality of data |
| Denial of Service | 5 | Potential disruptions to service operations |
In-Depth Analysis of Critical and Zero-Day Vulnerabilities
- DNS Protocol Zero-Day (CVE-2023-50868): This denial-of-service vulnerability, known from earlier disclosures, could severely impact system availability by exhausting CPU resources. Patched in this update, it previously affected various DNS implementations and posed a significant risk of service disruption.
- MSMQ Critical Vulnerability (CVE-2024-30080): A severe remote code execution flaw in Microsoft Message Queuing with a CVSS score of 9.8.
This critical issue, due to its low attack complexity and lack of need for authentication, allowed potential attackers to execute arbitrary code on affected servers. Organizations using MSMQ should verify if the service is enabled and if TCP port 1801 is listening, as recommended in Microsoft’s guidelines.
For vulnerabilities where immediate patching is not possible, it is crucial to implement alternative mitigation strategies.
These may include applying network filters or segmenting networks to restrict access to vulnerable systems, deploying additional monitoring tools to detect exploitation attempts, and educating users about potential phishing or social engineering attacks that could exploit the unpatched vulnerabilities.
Security Enhancements and Patch Impact
In June, Microsoft demonstrated its commitment to cybersecurity with targeted updates across its product suite. Notably, Windows received the highest number of patches, totaling 33, highlighting its pivotal role in both enterprise and personal computing environments. This substantial focus reflects the critical need to fortify systems against advanced threats.
Secure Boot and Windows Security Enhancements:
- Secure Boot Enhancements: The latest updates have improved Secure Boot’s validation processes. These enhancements are essential for verifying software integrity before the OS loads, effectively blocking rootkits and other malware at the boot level.
Windows Security Enhancements: Significant updates to Windows Defender have enhanced its threat detection capabilities. Updated signature databases and advanced heuristic algorithms improve the system’s proactive defense mechanisms.
Further, the integration with cloud-based analytics has been strengthened, enhancing real-time protection against new and evolving cyber threats.
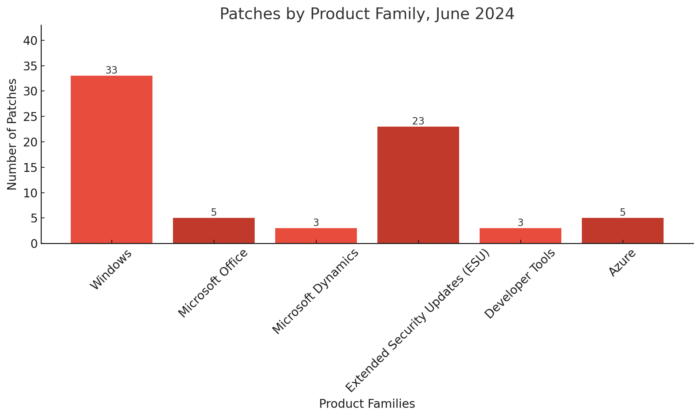
The extensive number of patches for Windows, as shown in the graph, underscores the importance of security updates in maintaining system integrity and safeguarding enterprise environments.
For a comprehensive understanding of how these updates enhance security, refer to the Microsoft Security Update Guide, which provides detailed insights into the improvements and strategic focus of the June 2024 Patch Tuesday.
Practical Guide: Implementing June 2024 Security Updates
- Prioritization and Testing: Assess and prioritize patches based on the severity and your environment’s exposure. Conduct thorough testing in a controlled environment to prevent disruptions.
- Deployment Strategies: Utilize automated tools like JetPatch for streamlined patch deployment, ensuring that patches are applied consistently and efficiently across all systems.
- Post-Deployment Monitoring: Continuously monitor the systems for any abnormalities post-update to ensure all patches have been successfully applied and are functioning as intended.
Conclusion
This update cycle targeted 51 key vulnerabilities, including critical remote code execution flaws and a notable zero-day vulnerability within the DNS protocol.
The vulnerabilities affected essential services like Microsoft Windows, Office, and Azure, highlighting the necessity for comprehensive security measures in today’s complex digital environment.
JetPatch can enhance IT security efficiency through complete automation of the patch management lifecycle, from assessing vulnerabilities to deploying patches. This automation not only reduces exposure to vulnerabilities but also improves operational efficiency.
Tailored to meet the specific needs of each organization, JetPatch provides meticulous control over patch scheduling and deployment tactics, ensuring that security measures are maintained and optimized.
For more information or to arrange a customized demonstration, visit our resources page to learn more or contact us to schedule a personalized demonstration today.


