Microsoft’s September 2024 Patch Tuesday covered a substantial total of 79 security vulnerabilities. This round of updates is particularly critical due to the inclusion of four zero-day vulnerabilities, three of which have been actively exploited.
The urgency of these patches cannot be overstated, as they aim to fortify systems against potential breaches. Here’s a quick summary of the vulnerabilities patched this month:
- Critical Vulnerabilities: 7
- Important Vulnerabilities: 71
- Moderate Vulnerabilities: 1
In-Depth Analysis of Critical Vulnerabilities
The September 2024 Patch Tuesday updates included a mix of vulnerabilities that pose significant risks, with zero-day vulnerabilities standing out due to their exploitation in the wild. This part of the blog dives deep into the analysis of these critical issues:
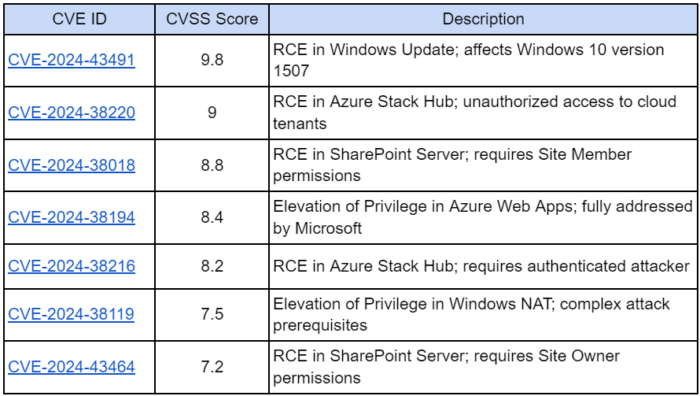
- CVE-2024-43491
- Severity: Critical
- CVSS Score: 9.8
Impact: This vulnerability was exploited in the wild. It resides in the Windows Servicing Stack and allows attackers to execute code remotely by reversing previously implemented security patches, particularly on Windows 10 version 1507 (Enterprise and IoT Enterprise LTSB editions).
- CVE-2024-38220
- Severity: Critical
- CVSS Score: 9.0
Impact: This vulnerability enables unauthorized access to Azure cloud tenants’ applications and content, potentially allowing attackers to perform unauthorized actions across the network.
- CVE-2024-38018
- Severity: Critical
- CVSS Score: 8.8
Impact: An authenticated attacker can execute code remotely on the SharePoint Server through network-based attacks, requiring at least Site Member level permissions.
- Additional Critical CVEs:
- CVE-2024-38194 (Azure Web Apps)
- CVE-2024-38216 (Azure Stack Hub)
- CVE-2024-38119 (Windows Network Address Translation (NAT))
- CVE-2024-43464 (Microsoft SharePoint Server)
Each of these vulnerabilities requires immediate attention due to their ability to allow attackers to perform privileged actions or execute code that can compromise the integrity and security of affected systems.
Comprehensive Breakdown of Vulnerability Types
The vulnerabilities addressed in September 2024 span a variety of types, showcasing the diverse threats faced by organizations and their IT infrastructures. Here’s a closer look at the distribution and classification of the vulnerabilities:
- Elevation of Privilege (EoP)
- Proportion: 38%
- Description: Allows attackers to gain higher-level permissions on a system.
- Examples: CVE-2024-38119, CVE-2024-38216
- Remote Code Execution (RCE)
- Proportion: 29.1%
- Description: Permits attackers to execute arbitrary code remotely.
- Examples: CVE-2024-43491, CVE-2024-38018
- Security Feature Bypass
- Proportion: 18%
- Description: Enables attackers to circumvent security mechanisms to access restricted data or execute unauthorized operations.
- Examples: CVE-2024-38217, CVE-2024-38226
- Information Disclosure
- Proportion: 7%
- Description: Involves the exposure of sensitive information to unauthorized parties.
- Examples: CVE-2024-37337, CVE-2024-37342
- Others
- Proportion: Remaining percentages
- Description: Includes less common vulnerabilities like Denial of Service (DoS), Cross-site Scripting (XSS), etc.
Zero-Day Vulnerabilities: A Closer Look
In the September 2024 Patch Tuesday release, Microsoft highlighted the presence of four zero-day vulnerabilities that were not only patched but had also seen exploitation in the wild. This section delves into each of these vulnerabilities, providing insights into their risks and the immediate necessity for patching:
- CVE-2024-43491
- Impact: This critical RCE vulnerability affects Windows 10 version 1507 (Enterprise and IoT Enterprise LTSB editions), where it allows remote code execution by reversing previously implemented security measures.
- Impact: This critical RCE vulnerability affects Windows 10 version 1507 (Enterprise and IoT Enterprise LTSB editions), where it allows remote code execution by reversing previously implemented security measures.
- CVE-2024-38014
- Impact: This vulnerability in the Windows Installer could allow an attacker with local access to gain SYSTEM-level privileges on the affected system.
- Impact: This vulnerability in the Windows Installer could allow an attacker with local access to gain SYSTEM-level privileges on the affected system.
- CVE-2024-38226
- Impact: This flaw allows an attacker to bypass Office macro policies by tricking a user into downloading and opening a specially crafted file, potentially leading to unauthorized actions.
- Impact: This flaw allows an attacker to bypass Office macro policies by tricking a user into downloading and opening a specially crafted file, potentially leading to unauthorized actions.
- CVE-2024-38217
- Impact: This vulnerability could allow an attacker to create a file that evades the Mark of the Web (MOTW) defenses, thereby compromising the security features of SmartScreen and Windows Attachment Services.
Each of these vulnerabilities has been exploited in the wild, emphasizing the critical need for timely patch application. Their diverse impacts showcase the various ways in which security can be compromised, from system-level access to bypassing security features designed to protect against untrusted files.
Sector-Specific Impact Analysis
The September 2024 Patch Tuesday release had broad implications across multiple sectors, particularly impacting Microsoft IoT and Enterprise Security environments. This section provides an analysis of how the vulnerabilities patched this month affect these specific sectors:
- Microsoft IoT (Internet of Things)
- Vulnerabilities like CVE-2024-43491 and CVE-2024-38018 have profound implications for IoT devices, especially those running on older versions of Windows 10 Enterprise. The remote execution capabilities can severely compromise IoT device security, potentially leading to unauthorized control or data theft.
- Vulnerabilities like CVE-2024-43491 and CVE-2024-38018 have profound implications for IoT devices, especially those running on older versions of Windows 10 Enterprise. The remote execution capabilities can severely compromise IoT device security, potentially leading to unauthorized control or data theft.
- Enterprise Security
- Critical vulnerabilities in Azure and SharePoint (CVE-2024-38220, CVE-2024-38018, CVE-2024-38194) highlight the risks to enterprise infrastructures, particularly in cloud and shared services environments. These vulnerabilities could allow attackers to bypass authentication measures, execute code remotely, or gain elevated privileges, all of which could lead to data breaches or operational disruptions.
- Critical vulnerabilities in Azure and SharePoint (CVE-2024-38220, CVE-2024-38018, CVE-2024-38194) highlight the risks to enterprise infrastructures, particularly in cloud and shared services environments. These vulnerabilities could allow attackers to bypass authentication measures, execute code remotely, or gain elevated privileges, all of which could lead to data breaches or operational disruptions.
- Impact on Industry-Specific Applications
- SQL Server and SharePoint vulnerabilities (CVE-2024-38018, CVE-2024-38194) pose significant risks to industries reliant on large databases and collaborative platforms, such as finance and healthcare, where data integrity and security are paramount.
This sector-specific focus helps organizations understand the potential risks and encourages targeted patch management strategies to mitigate these vulnerabilities effectively.
Practical Security Updates Implementation Guide
For a streamlined update process, here’s a condensed guide focusing on key actions:
- Audit and Prioritization:
- Identify systems using affected versions.
- Prioritize patches based on CVE severity and system criticality.
- Testing the Patches:
- Deploy patches in a controlled test environment.
- Monitor for compatibility issues and performance impacts.
- Deployment:
- Implement patches during off-peak hours to minimize business disruption.
- Utilize management tools like WSUS or SCCM for efficient rollout.
- Monitoring and Response:
- Keep an eye on network activity and security logs post-deployment.
- Update incident response strategies based on new insights from the deployment phase.
- Documentation:
- Keep detailed records of the deployment process for compliance and auditing.
- Generate reports on deployment outcomes and unresolved vulnerabilities.
Conclusion
In light of the numerous vulnerabilities addressed in Microsoft’s September 2024 Patch Tuesday, it’s evident that proactive and efficient patch management is crucial. The variety of critical and zero-day vulnerabilities underscores the evolving landscape of cybersecurity threats.
JetPatch enhances IT security by automating the entire patch management lifecycle—from vulnerability assessment to patch deployment. This automation not only minimizes vulnerability risks but also boosts operational efficiency.
We offer customized control over patch scheduling and deployment strategies, tailored to each organization’s unique needs, ensuring optimized and consistent security measures.
For more detailed information or to arrange a personalized demonstration, contact us today.


